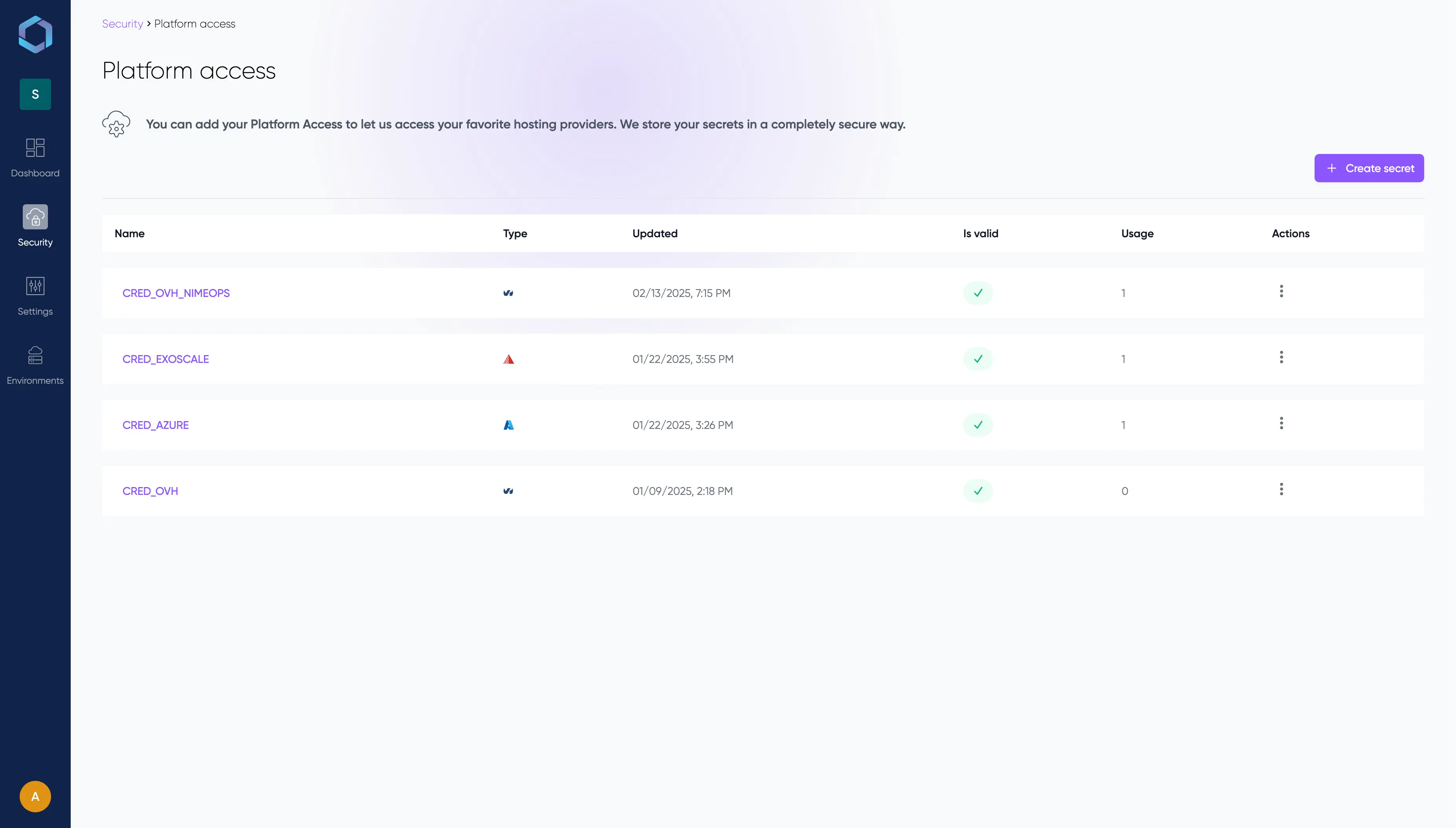
Platform Access
You can find "Platform Access" in the top "Security" menu when a project is selected.
This is where you'll store all your access credentials to your cloud platforms. These secrets can then be used to create your environments. Your secrets are securely stored within LayerOps.
One of the special characteristics of LayerOps is that we use your cloud platform accounts directly. LayerOps doesn't charge for resource usage; you get the real price of your consumption directly from your cloud providers.
3DS Outscale
To generate access keys, please follow the official documentation on 3DS Outscale documentation.
Once you have your Access Key ID and Secret Key, you can create your platform access secret.
AWS
Follow this documentation to create a new user on your AWS account and then create a dedicated policy for this user.
Provide user access to the AWS Management ConsoleHere's the recommended policy to assign to the new user on AWS:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2:DescribeAccountAttributes",
"iam:GetUser"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"ec2:DescribeAddresses",
"ec2:DescribeAddressesAttribute",
"ec2:DescribeImages",
"ec2:DescribeInstanceAttribute",
"ec2:DescribeInstanceCreditSpecifications",
"ec2:DescribeInstances",
"ec2:DescribeInternetGateways",
"ec2:DescribeKeyPairs",
"ec2:DescribeLaunchTemplates",
"ec2:DescribeNatGateways",
"ec2:DescribeNetworkInterfaces",
"ec2:DescribeRouteTables",
"ec2:DescribeSecurityGroupRules",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSubnets",
"ec2:DescribeTags",
"ec2:DescribeVolumes",
"ec2:DescribeVpcAttribute",
"ec2:DescribeVpcs"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"ec2:AllocateAddress",
"ec2:AssignPrivateNatGatewayAddress",
"ec2:AssociateNatGatewayAddress",
"ec2:AssociateRouteTable",
"ec2:AttachInternetGateway",
"ec2:AttachVolume",
"ec2:AuthorizeSecurityGroupEgress",
"ec2:AuthorizeSecurityGroupIngress",
"ec2:CopyImage",
"ec2:CreateInternetGateway",
"ec2:CreateKeyPair",
"ec2:CreateNatGateway",
"ec2:CreateRoute",
"ec2:CreateRouteTable",
"ec2:CreateSecurityGroup",
"ec2:CreateSubnet",
"ec2:CreateTags",
"ec2:CreateVolume",
"ec2:CreateVpc",
"ec2:RunInstances",
"ec2:StartInstances"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"ec2:DeleteInternetGateway",
"ec2:DeleteKeyPair",
"ec2:DeleteNatGateway",
"ec2:DeleteRoute",
"ec2:DeleteRouteTable",
"ec2:DeleteSecurityGroup",
"ec2:DeleteSubnet",
"ec2:DeleteTags",
"ec2:DeleteVolume",
"ec2:DeleteVpc",
"ec2:DeregisterImage",
"ec2:DisassociateNatGatewayAddress",
"ec2:DisassociateRouteTable",
"ec2:DetachInternetGateway",
"ec2:DetachVolume",
"ec2:ImportKeyPair",
"ec2:ModifyVpcAttribute",
"ec2:ReleaseAddress",
"ec2:RevokeSecurityGroupEgress",
"ec2:RevokeSecurityGroupIngress",
"ec2:StopInstances",
"ec2:TerminateInstances",
"ec2:UnassignPrivateNatGatewayAddress"
],
"Resource": "*",
"Condition": {
"StringEqualsIfExists": {
"ec2:ResourceTag/CreatedBy": "user"
}
}
}
]
}To generate access keys for your new LayerOps user, please follow the official AWS documentation.
Once you have your Access Key ID and Secret Key, you can create your platform access secret.
Azure
Get your Subscription ID
Navigate to your Azure portal's subscription page.
You will find all subscriptions activated on your account on this page. Select the one you want to use and note the Subscription ID.
Create an Application in Azure Active Directory
Navigate to Microsoft Entra portal
- Select "Applications" in the menu bar
- Select "App Registration"
- Click the "New registration" button at the top to add a new Application, and specify:
- Name - this is a friendly identifier and can be anything (e.g. "LayerOps-Creds")
- Supported Account Types - this should be set to "Accounts in this organizational directory only (single-tenant)"
- Redirect URI - Value can be left blank
To retrieve Application informations, navigate to this Microsoft AAD IAM Section
- Click on on the Applicate named in previous step
You'll need to take note of the "Application (client) ID" and the "Directory (tenant) ID", which you can use for the values of
- Application (client) ID
- Tenant ID respectively.
Generating a Client Secret
- Select "Certificates & secrets"
- Generate a new Client Secret
- Enter a description
- Select an Expiry Date
- Click "Add"
Granting the Application Access
Navigate to your Azure Subscription Blade
- Select the subscription
- Click "Access Control (IAM)"
- Click "Add > Add role assignment"
- Specify a Role which grants the appropriate permissions needed (e.g., "Contributor" will grant Read/Write on all resources in the Subscription)
Google Cloud Platform
Follow this documentation to create a service account and get your credentials as a JSON file.
To let LayerOps create and manage GCP resources, select the role Compute Admin.
Once you have retrieved the JSON file, you can create your platform access secret and upload this file.
LXD
To connect LayerOps to a remote LXD server, you need to generate a trust token that will be used to establish a secure connection.
Prerequisites
- A running LXD server
- SSH access to the LXD server
lxccommand line tool installed on the server
Generating the Trust Token
- Connect to your LXD server via SSH
- Run the following command to generate a trust token:
lxc config trust add --name layerops - The command will output a token that looks like this:Make sure to copy this token as it will only be shown once.
token: 4cc0aadf5fca4f8b82b3b3f8e4f3c9a2
Configuring in LayerOps
Once you have the token, you can create your platform access in LayerOps by entering:
- URL: The URL of your LXD server (e.g.,
https://your-server:8443) - API Token: The token generated in the previous step
OVH Cloud
To configure OVH Cloud access in LayerOps, you'll need to retrieve or create the following credentials:
- Username
- Password
- Tenant ID
- Tenant Name
Creating an OpenStack User
- Log in to your OVH Control Panel
- Go to "Public Cloud" section
- Select your project
- Navigate to "Users & Roles" in the left menu
- Click on "Add user" button
- Choose a description for your user (e.g., "LayerOps")
- Select the "Administrator" role
- Click "Confirm"
Once created, you'll see:
- Your username (usually starts with "user-")
- A password - make sure to save it as it will only be shown once
Getting Tenant Information
The tenant ID and tenant name can be found in your OpenStack RC file:
- Still in your OVH Public Cloud project
- Click on the "OpenStack" button in the top right corner
- Click on "Download an OpenStack configuration file"
- Open the downloaded file
- Look for these lines:
export OS_PROJECT_ID="xxx"- This is your tenant IDexport OS_PROJECT_NAME="xxx"- This is your tenant name
Configuring in LayerOps
Once you have all the required information, you can create your platform access in LayerOps by entering:
- Username: The user you created (starts with "user-")
- Password: The password you saved during user creation
- Tenant ID: The ID found in the RC file
- Tenant Name: The name found in the RC file
Scaleway
To configure Scaleway access in LayerOps, you'll need to provide:
- Project ID
- Access Key
- Secret Key
Getting your Project ID
- Log in to your Scaleway Console
- Go to the Organization Dashboard
- Click on the "Projects" tab
- Find your project in the list
- Copy the Project ID (it looks like:
12345678-1234-1234-1234-123456789012)
Creating API Keys
- Click Identity and Access Management (IAM) on the top-right of your Organization Dashboard in the Scaleway console
- Click the API keys tab
- Click Generate API key
- Select yourself as the bearer of the API key
- Enter a description (e.g., "LayerOps")
- Choose an expiration date (or select "Never" if you don't want the key to expire)
- Click Generate API Key
You'll receive:
- An Access Key (starts with
SCWXXXXXXXXXXXXXXXXX) - A Secret Key - make sure to save it as it will only be shown once
Configuring in LayerOps
Once you have all the required information, you can create your platform access in LayerOps by entering:
- Project ID: The ID copied from your project settings
- Access Key: The generated access key
- Secret Key: The secret key you saved during API key generation
Exoscale
To configure Exoscale access in LayerOps, you'll need to provide:
- Access Key
- Secret Key
Creating an API Key
- Log in to your Exoscale Portal
- Navigate to IAM, then KEYS
- Click "Add"
- In the Key creation form:
- Enter a name for your key (e.g., "LayerOps")
- Select a Role (if you want unrestricted access, create a role with default settings)
- Click "Create"
You'll receive:
- An API Key - starts with "EXO"
- An API Secret - make sure to save it as it will only be shown once
Configuring in LayerOps
Once you have the credentials, you can create your platform access in LayerOps by entering:
- Access Key: The API Key you received
- Secret Key: The API Secret you saved during creation
Infomaniak
To configure Infomaniak access in LayerOps, you'll need to provide:
- Username
- Password
- Tenant ID
- Tenant Name
Creating an OpenStack User
- Log in to your Infomaniak Manager
- Go to "Public Cloud"
- Select your public cloud
- Click on "Manage" in your project "OpenStack users" column
- Click "Add an OpenStack user"
- Enter a description for your user (e.g., "LayerOps")
- Enter a password for your user - make sure to save it, you will need it to create your platform access
- Confirm the openstack user creation
Getting Tenant Information
The tenant ID and tenant name can be found in your OpenStack RC file:
- In the users list, find your user and click on three dots to the right of your user
- Click "Download the OpenStack RC file"
- Open the downloaded file
- Look for these lines:
export OS_PROJECT_ID="xxx"- This is your tenant IDexport OS_PROJECT_NAME="xxx"- This is your tenant name
Configuring in LayerOps
Once you have all the required information, you can create your platform access in LayerOps by entering:
- Username: The user you created (starts with "PCU-")
- Password: The password you saved during user creation
- Tenant ID: The ID found in the RC file
- Tenant Name: The name found in the RC file